Tailor-Made Privacy-Safe Data for Your Entire Enterprise
In today’s data-driven economy, privacy concerns around AI have reached new heights, leaving enterprises grappling with the question of how to effectively monetize their valuable data. With Bornio’s AI-powered, data engineer friendly solution allows you to harness the full spectrum of your data’s potential with just a few simple steps.
Realistic High Quality Data
Policy-Driven, Customizable
Regulatory Compliant
Faster Data
Service Requests
Reduced Cost
and Complexity
Supercharge Data For Pre-Training, Fine-Tuning Of Your AI Models
Data access is critical whether you are building a new model or using a foundational model. Bornio removes traditional access barriers that prevents data scientists from creating effective models.
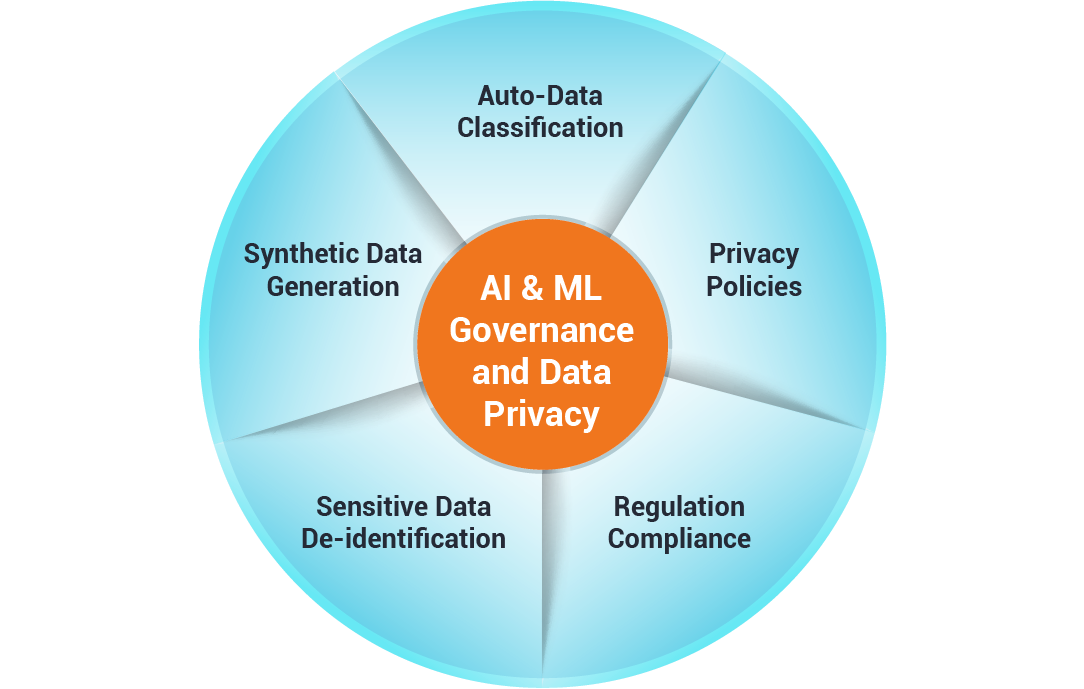
Auto-Discovers and Classifies Sensitive Data (PII) Across Data Sources
Instead of painstakingly trying to identify potential PII data in your datasets, Bornio does so autonomously. Removing unnecessary time-consuming work that would otherwise taking up a large portion of your time.
Recommends Policies for Granular Control Over Data Generation For Specific Use-Cases
Our cutting-edge tool gives you granular control for targeted privacy sensitive use cases. This automated capability simplifies operational efficiency while ensuring data privacy, and data integrity.
Leverages Proprietary Universal Data Generator as well as Third-Party Foundational Models
Bornio’s unique engine is also integrated with the latest foundational models to generate the most representative data for your AI projects
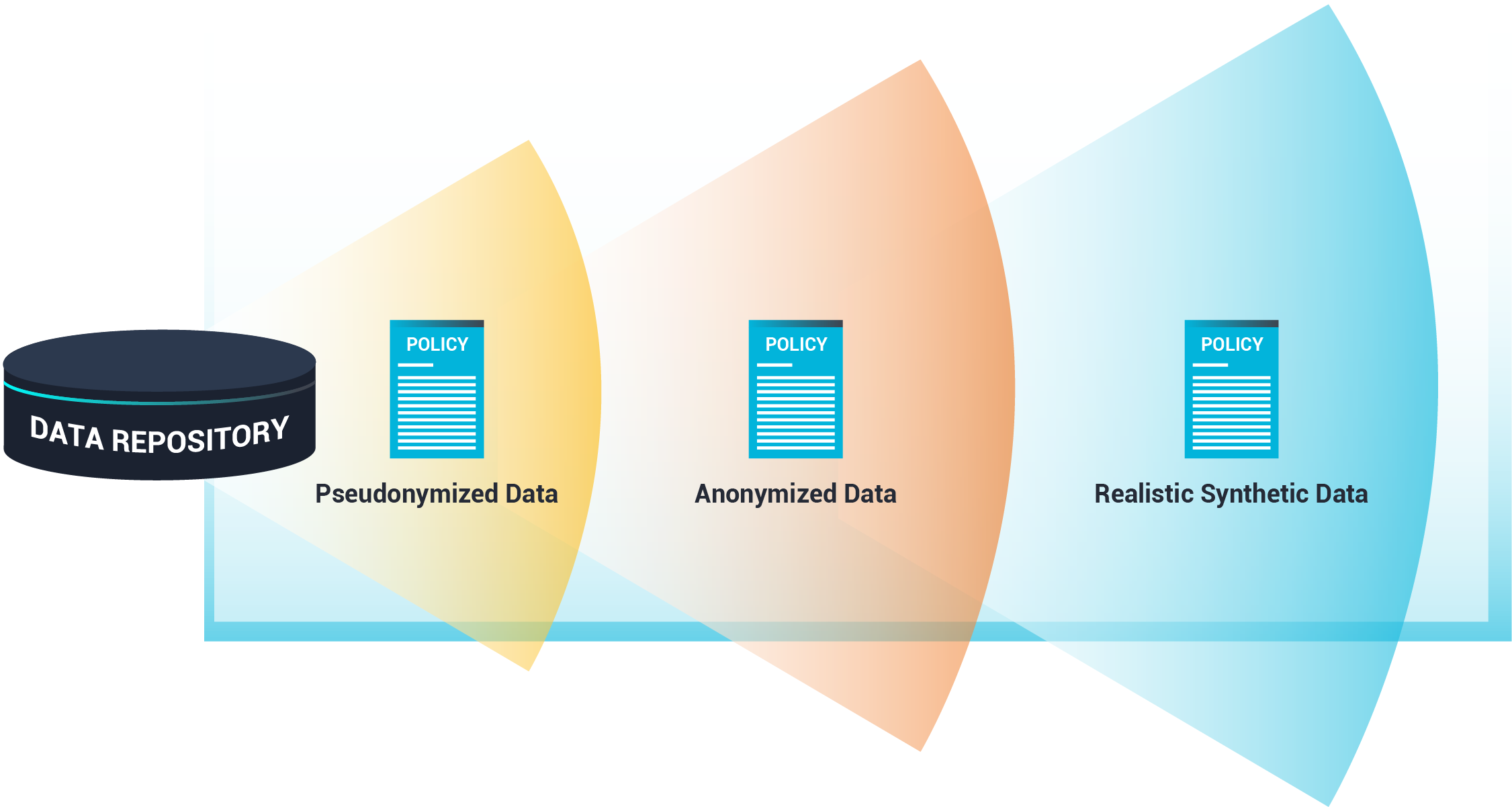
Retains the Same Properties as Original Data Without Compromising Privacy
Unlike other tools that strip away key insights resulting in data drift and bias, Bornio retains the critical properties of your original data without violating privacy policies. All this while maintaining data usefulness and relevance, assuring you an uncompromised, seamless operation.
Enterprise Data Transformed for Every Data-Driven Applications
AI, ML, Data Science
Maintain data privacy and consistency of your data sources throughout the model-training lifecycle.
Reduce model-training time and increase accuracy by deriving realistic data from production.
Business Intelligence, Analytics
Auto-generate granular policies for different data consumers (i.e., personas) allowing users to share sensitive data on a need-to-know basis.
Maximize privacy and data usability with a rich collection of privacy protection methods.
Application Dev, Test, & Triage
Integrate production-derived data for application development, testing, and triaging into a CI/CD process.
Preserve inter-column and inter-table value consistency and referential integrity of data.
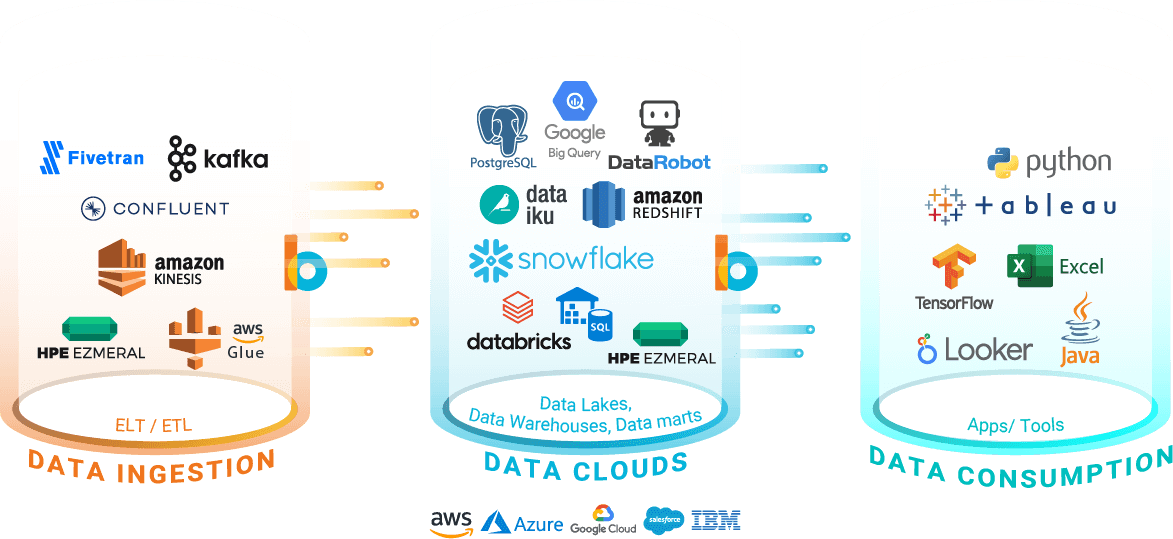
Natively Embedded Anywhere In The Modern Data Clouds & Pipelines