Bornio
Auto-Transform Sensitive Data for any Enterprise-Wide Use Cases
Our innovative Data Privacy solution utilize cutting-edge technology to automatically de-identify sensitive production data, creating a version of this data that is policy and regulation compliant, user-specific, and purpose-ready. With Bornio, your data is trusted and useful for a variety of high-quality tasks, such as application testing, AI model training and validation, BI analytics, and more. And because our solutions are deployed into your own cloud environment, they actively protect your data by applying a policy based on de-identification only to sensitive fields throughout the entire data flow.
HOW IT WORKS
Connect with Your Data Cloud, Observe, and Classify Sensitive data
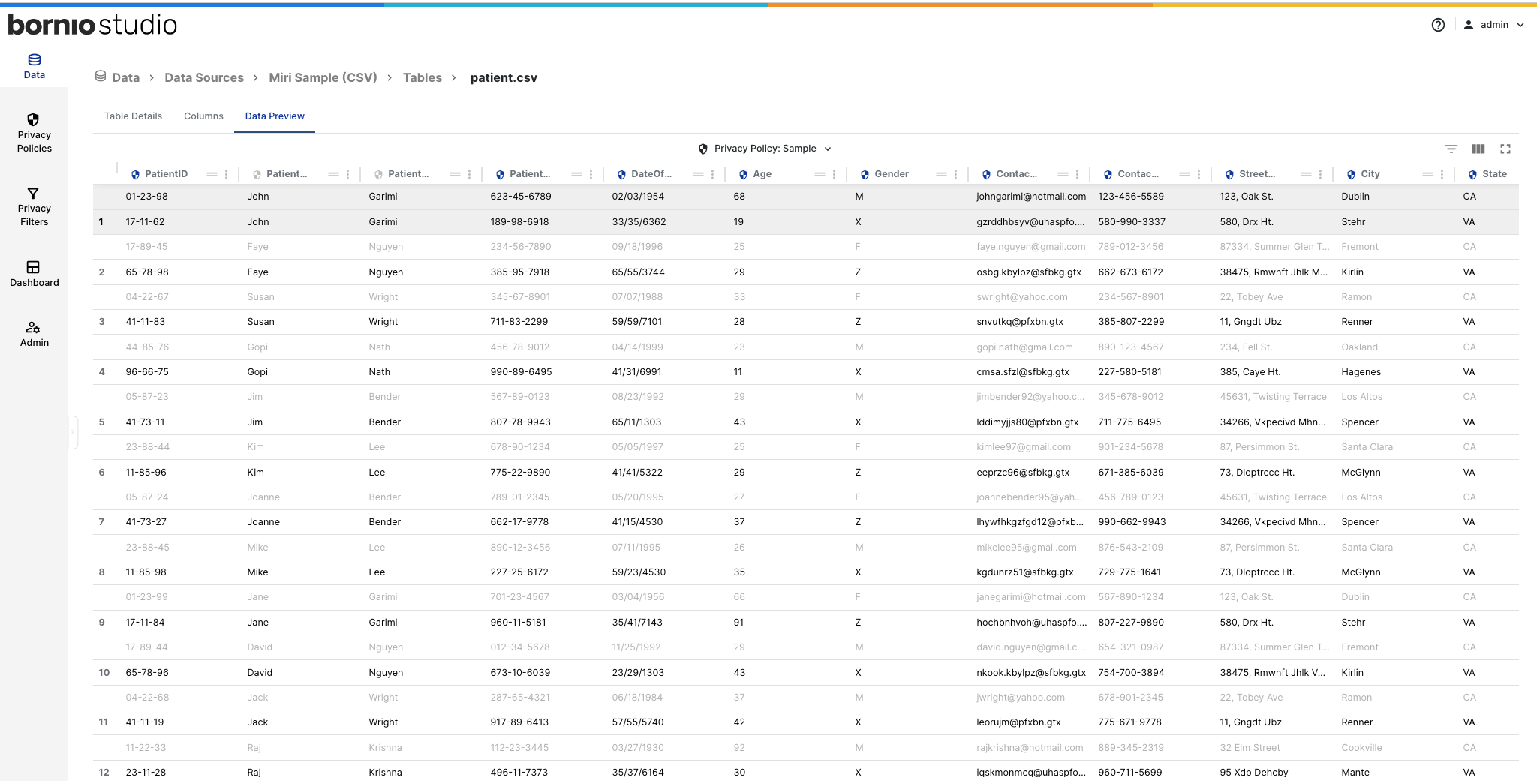
Using state-of-the-art automated observability and discovery techniques, Bornio is able to generate transformed data that is as realistic as possible while still preserving the privacy of sensitive data at its source.
Get Policy Recommendations Based on User Personas
Adding role-based policies is an important way to comply with any regulatory requirements and maximize data security within your organization. These policies can be customized according to your specific privacy requirements, providing a flexible framework that adapts as your organization evolves. With well-considered, tailored policy recommendations in place, you can rest easy knowing that your data is safe from unauthorized access and use.
Leverage the Rich Library of Data Protection Methods
Bornio offers a truly unique framework with an extensive library of flexible data protection methods and features that allow you to tailor your approach specifically to your needs. Our flexible framework allows users to easily select from a wide range of methods, from basic masking to more advanced techniques such as encryption-decryption-de-identification flows and conditional protection. By providing these options and supporting features such as data hardening, we give businesses the tools they need to ensure that their data is always protected, no matter how it is being used or accessed.
HOW IT WORKS
Connect with Your Data Cloud, Observe, and Classify Sensitive data
Using state-of-the-art automated observability and discovery techniques, Bornio is able to generate transformed data that is as realistic as possible while still preserving the privacy of sensitive data at its source.
Get Policy Recommendations Based on User Personas
Adding role-based policies is an important way to comply with any regulatory requirements and maximize data security within your organization. These policies can be customized according to your specific privacy requirements, providing a flexible framework that adapts as your organization evolves. With well-considered, tailored policy recommendations in place, you can rest easy knowing that your data is safe from unauthorized access and use.
Leverage the Rich Library of Data Protection Methods
Bornio offers a truly unique framework with an extensive library of flexible data protection methods and features that allow you to tailor your approach specifically to your needs. Our flexible framework allows users to easily select from a wide range of methods, from basic masking to more advanced techniques such as encryption-decryption-de-identification flows and conditional protection. By providing these options and supporting features such as data hardening, we give businesses the tools they need to ensure that their data is always protected, no matter how it is being used or accessed.
A Power Tool for Data and Privacy Engineers
User-Role Specific
Granular policies for persona-specific data in the right format for the role/user. Designed for need-to-know.
Real-World Data
Privacy-preserving, real-world-like data for all data-driven applications.
Protection Method Library
Extensive library of protection methods for a variety of PHI, PII data, and use cases.
Encoded Regulations
Privacy Regulations such as PCI, HIPAA, GDPR, and more are encoded into policy models to enable policy recommendations suited for the purpose.
Data Consistency
In-column, Inter-column value consistency, Inter-table referential integrity.
Production-derived
High-fidelity, shape preserving data for AI / ML model training, testing and validation and Analytics.
Deployed in Data Clouds
All common File, Database, Data Lakes, Data Warehouses, Lakehouses and Streaming Data (Kafka).
Centralized control
Centralized, consistent control over the specification of enterprise privacy policies. How each data element in a dataset should be protected is encoded in a privacy policy.
Support for SDLC stages
This brings software engineering rigor to the development, testing and push-to-production of Bornio Data Privacy Policies using a low-code / no-code approach.
Embed Bornio in Modern Data Clouds

Data for Purpose, with Configurable Solution
Generating synthetic data is expensive, complex
Data preparation takes more than 40% of model development time
Data may not represent real-world scenarios
Impacting model training, validation, and accuracy
Compliant data, preserving shape, format, and referential integrity
Non-overlapping data sets that facilitate real-world training, testing
Mathematically-proven algorithms to maximize privacy and data quality
Improving model accuracy while reducing training and validation times
Data masking leads to diminishing business insights and operational efficiency
Granular policies per data consumer personas on a need-to-know basis
A rich collection of privacy protection methods – from simple to sophisticated, to meet the most stringent regulatory needs
Policymakers and data owners can formally review, validate, and sign-off
Continuous compliance with monitoring, logging, and risk monitoring
Manually labored dummy or fake data does not represent production scenarios accurately
Developers and SREs struggle to automate CICD
Elongating application development life cycle
Production-derived data maintain high-fidelity to production data in terms of form, shape, and semantics preservation
Shape data sizes (subset, supersets), entity-relations tracing
In-column, Inter-column, and inter-table value consistency and referential integrity preserve data relationships in production data

